Cybersecurity researchers have shed light on a previously undocumented threat actor called TA585 that has been observed delivering an off-the-shelf malware called MonsterV2 via phishing campaigns.
The Proofpoint Threat Research Team described the threat activity cluster as sophisticated, leveraging web injections and filtering checks as part of its attack chains.
“TA585 is notable because it appears to own its entire attack chain with multiple delivery techniques,” researchers Kyle Cucci, Tommy Madjar, and Selena Larson said. “Instead of leveraging other threat actors – like paying for distribution, buying access from initial access brokers, or using a third-party traffic delivery system – TA585 manages its own infrastructure, delivery, and malware installation.”
MonsterV2 is a remote access trojan (RAT), stealer, and loader, which Proofpoint first observed being advertised on criminal forums in February 2025. It’s worth noting that MonsterV2 is also called Aurotun Stealer (a misspelling of “autorun”) and has been previously distributed via CastleLoader (aka CastleBot).
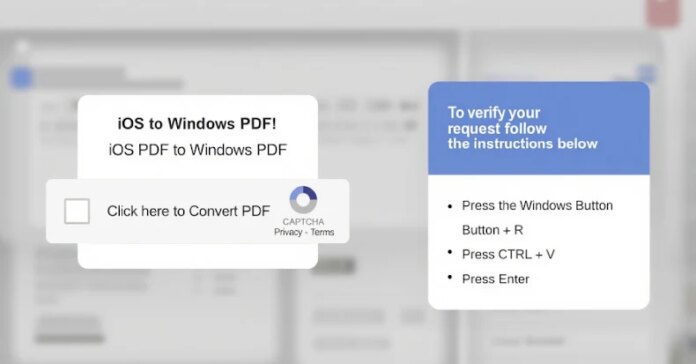
Phishing campaigns distributing the malware have been observed using U.S. Internal Revenue Service (IRS) themed lures to trick users into clicking on fake URLs that direct to a PDF, which, in turn, links to a web page employing the ClickFix social engineering tactic to activate the infection by running a malicious command in the Windows Run dialog or PowerShell terminal. The PowerShell command is designed to execute a next-stage PowerShell script that deploys MonsterV2.
Subsequent attack waves detected in April 2025 have resorted to malicious JavaScript injections on legitimate websites that serve fake CAPTCHA verification overlays to initiate the attack via ClickFix, ultimately leading to the delivery of the malware via a PowerShell command.
Initial iterations of this campaign distributed Lumma Stealer, before TA585 switched to MonsterV2 in early 2025. Interestingly, the JavaScript inject and the associated infrastructure (intlspring[.]com) have also been linked to the distribution of Rhadamanthys Stealer.
A third set of campaigns undertaken by TA585 has made use of email notifications from GitHub that are triggered when tagging GitHub users in bogus security notices that contain URLs leading to actor-controlled websites.
Both the activity clusters – that revolve around web injects and phony GitHub alerts — have been associated with CoreSecThree, which, according to PRODAFT, is a “sophisticated framework” that’s known to be active since February 2022 and has been “consistently” used to propagate stealer malware.
MonsterV2 is a full-featured malware that can steal sensitive data, act as a clipper by replacing cryptocurrency addresses in the infected systems’ clipboard with threat actor-provided wallet addresses, establish remote control using Hidden Virtual Network Computing (HVNC), receive and execute commands from an external server, and download additional payloads.
The malware is sold by a Russian-speaking actor for $800 USD per month for the “Standard” edition, while the “Enterprise” version, which comes with stealer, loader, HVNC, and Chrome DevTools Protocol (CDP) support, costs $2,000 per month. A notable aspect of the stealer is that it avoids infecting Commonwealth of Independent States (CIS) countries.
MonsterV2 is typically packed using a C++ crypter called SonicCrypt, thereby allowing it to evade detection by running a series of anti-analysis checks prior to decrypting and loading the payload.
Once launched, the malware decrypts and resolves the Windows API functions crucial to its functioning, in addition to elevating its privileges. It then proceeds to decode an embedded configuration to connect to the command-and-control (C2) server, as well as determine its next course of action based on the parameters set –
- anti_dbg, if set to True, the malware attempts to detect and evade debuggers in use
- anti_sandbox, if set to True, the malware attempts to detect sandboxes and execute some rudimentary anti-sandbox techniques
- aurotun (it’s this misspelling that has given it the name Aurotun Stealer), if set to True, the malware attempts to set up persistence on the host
- priviledge_escalation, if set to True, the malware attempts to elevate its privileges
If the malware successfully establishes contact with the C2 server, it sends basic system information and the system’s geolocation by sending a request to “api.ipify[.]org.” The response from the server contains the command to be executed on the host. Some of the supported features are listed below –
- Execute infostealer functionality and exfiltrate data to the server
- Execute an arbitrary command via cmd.exe or PowerShell
- Terminate, suspend, and resume target processes
- Establish an HVNC connection to the infected system
- Take screenshots of the desktop
- Start a keylogger
- Enumerate, manipulate, copy, and exfiltrate files
- Shut down or crash the system
- Download and execute next-stage payloads like StealC, Remcos RAT
“This activity was not correlated with TA585, however. Notably, with StealC, the MonsterV2 payloads were configured to use the same C2 server as the dropped StealC payload,” Proofpoint said. “TA585 is a unique threat actor with advanced capabilities for targeting and delivery. As the cybercrime threat landscape is constantly changing, TA585 has adopted effective strategies for filtering, delivery, and malware installation.”
Source link