
North Korean hackers have adopted the ‘EtherHiding’ technique that leverages smart contracts to host and deliver malware in social engineering campaigns that steal cryptocurrency.
Google Threat Intelligence Group (GTIG) says that a DPRK nation state threat actor, tracked internally as UNC5342, has been employing EtherHiding since February in Contagious Interview operations.
The researchers note that this is the first time they saw a state-backed hacker group using this method.
First described by Guardio Labs in 2023, EtherHiding is a malware distribution technique where payloads are embedded within smart contracts on a public blockchain (Binance Smart Chain or Ethereum). The threat actor can thus host malicious scripts and retrieve them when needed.
Due to how blockchains work, EtherHiding offers anonimity, resistance to takedown actions and allows flexible payload updating, all at a very low cost. Furthermore, fetching the payloads is possible through read-only calls that leave no visible transaction history, adding stealth to the process.
DPRK ops on the blockchain
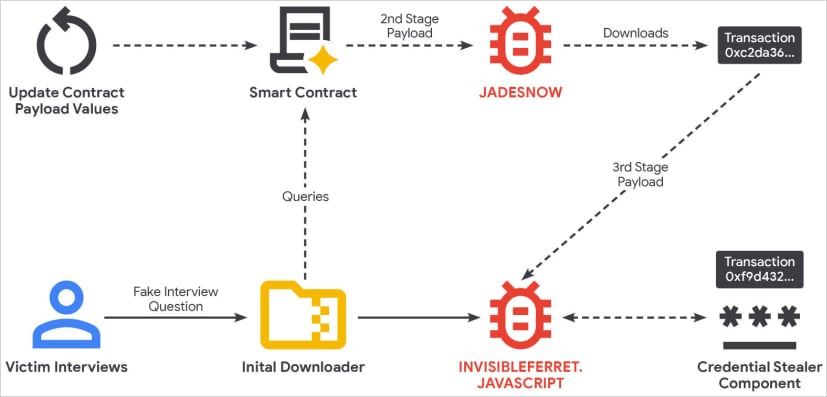
The attacks typically begin fake job interviews, a hallmark for DPRK’s hallmark social engineering tactics, from carefully fabricated entities (BlockNovas LLC, Angeloper Agency, SoftGlide LLC) targeting software and web developers.
The victim is tricked into running code, as part of the interview’s technical assessment, that executes a JavaScript downloader.
The researchers say that “the smart contract hosts the JADESNOW downloader that interacts with Ethereum to fetch the third-stage payload,” which is a JavaScript version of the InvisibleFerret malware typically used for long-term espionage.
GTIG notes that the payload runs in memory and may ask Ethereum for an another component that steals credentials.
According to the researchers, the hackers can use JADESNOW to retrieve a payload from either Ethereum or the BNB Smart Chain, which makes analysis more difficult.
“It is unusual to see a threat actor make use of multiple blockchains for EtherHiding activity; this may indicate operational compartmentalization between teams of North Korean cyber operators,” GTIG says.
Source: Google
“The transaction details show that the contract has been updated over 20 times within the first four months, with each update costing an average of $1.37 USD in gas fees,” explains GTIG.
“The low cost and frequency of these updates illustrate the attacker’s ability to easily change the campaign’s configuration,” the researchers say.
The malware runs in the background and listens for incoming commands from its command and control (C2), like executing arbitrary commands and exfiltrating files in ZIP form to an external server or Telegram.
The credential stealer component targets passwords, credit cards, and cryptocurrency wallet (MetaMask and Phantom) information stored on web browsers like Chrome and Edge.
The adoption of EtherHiding by North Korean threat actors is a notable development that creates campaign tracking and disruption complexities.
Individuals targeted with alluring job offers should remain cautious when asked to download anything, and test files in isolated environments first.
GTIG suggests that administrators place download restrictions for risky file types (.EXE, .MSI, .BAT, .DLL) on Chrome Enterprise, assume full control of browser updates, and place strict web access and script execution policies.
Source link






