
Oracle has silently fixed an Oracle E-Business Suite vulnerability (CVE-2025-61884) that was actively exploited to breach servers, with a proof-of-concept exploit publicly leaked by the ShinyHunters extortion group.
The flaw was addressed with an out-of-band security update released over the weekend, which Oracle said could be used to access “sensitive resources.”
“This Security Alert addresses vulnerability CVE-2025-61884 in Oracle E-Business Suite,” reads Oracle’s advisory.
“This vulnerability is remotely exploitable without authentication, i.e., it may be exploited over a network without the need for a username and password. If successfully exploited, this vulnerability may allow access to sensitive resources.”
However, Oracle did not disclose that the flaw was actively exploited in attacks or that a public exploit had been released.
Multiple researchers, customers, and BleepingComputer have confirmed that the security update for CVE-2025-61884 now addresses the pre-authentication Server-Side Request Forgery (SSRF) flaw used by the leaked exploit.
BleepingComputer reached out to Oracle more than six times for comment about the updates and the lack of disclosure regarding active exploitation, but received either no reply or they declined to comment.
The confusing mess of Oracle zero-days
Earlier this month, Mandiant and Google began tracking a new extortion campaign in which companies received emails claiming sensitive data had been stolen from their Oracle E-Business Suite (EBS) systems.
These emails came from the Clop ransomware operation, which has a long history of exploiting zero-day flaws in widespread data theft attacks.
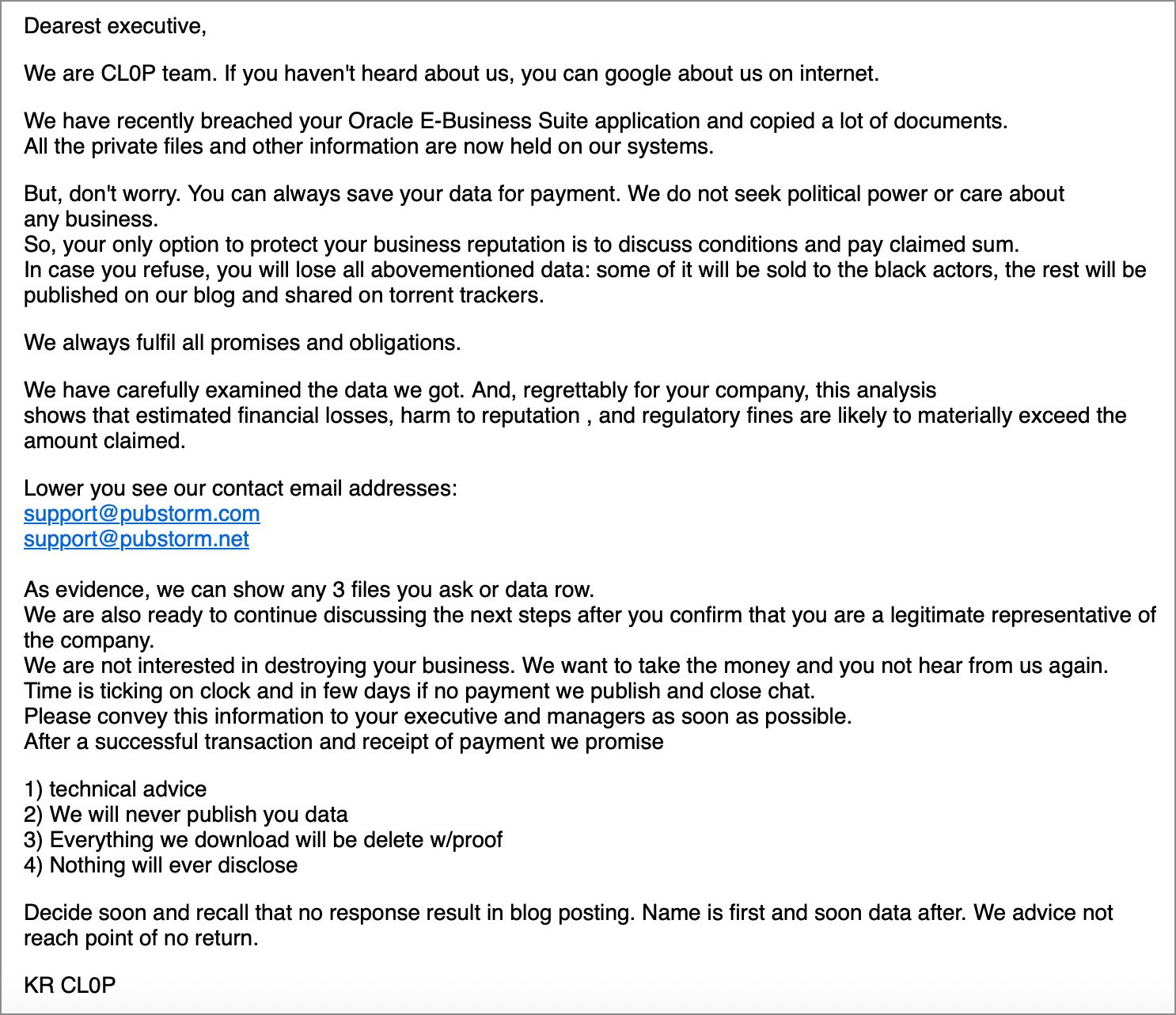
While Clop would not share details about the attack, they confirmed to BleepingComputer that they were behind the emails and claimed a new Oracle flaw was exploited in the data theft attacks.
“Soon all will become obvious that Oracle bugged up their core product and once again, the task is on clop to save the day,” the extortion gang told BleepingComputer.
In response to the extortion emails, Oracle stated that Clop was exploiting an EBS flaw that was patched in July 2025, advising customers to ensure the latest Critical Patch Updates were installed.
Soon after, another group of threat actors, known as Scattered Lapsus$ Hunters, also known as ShinyHunters, released an Oracle E-Business Suite exploit on a Telegram channel that was being used to extort Salesforce customers.
Oracle later confirmed on October 5 that a new zero-day (CVE-2025-61882) affected EBS and released an emergency patch. Notably, one of the indicators of compromise (IOCs) in Oracle’s advisory referenced the exploit released by Scattered Lapsus$ Hunters, suggesting a connection.
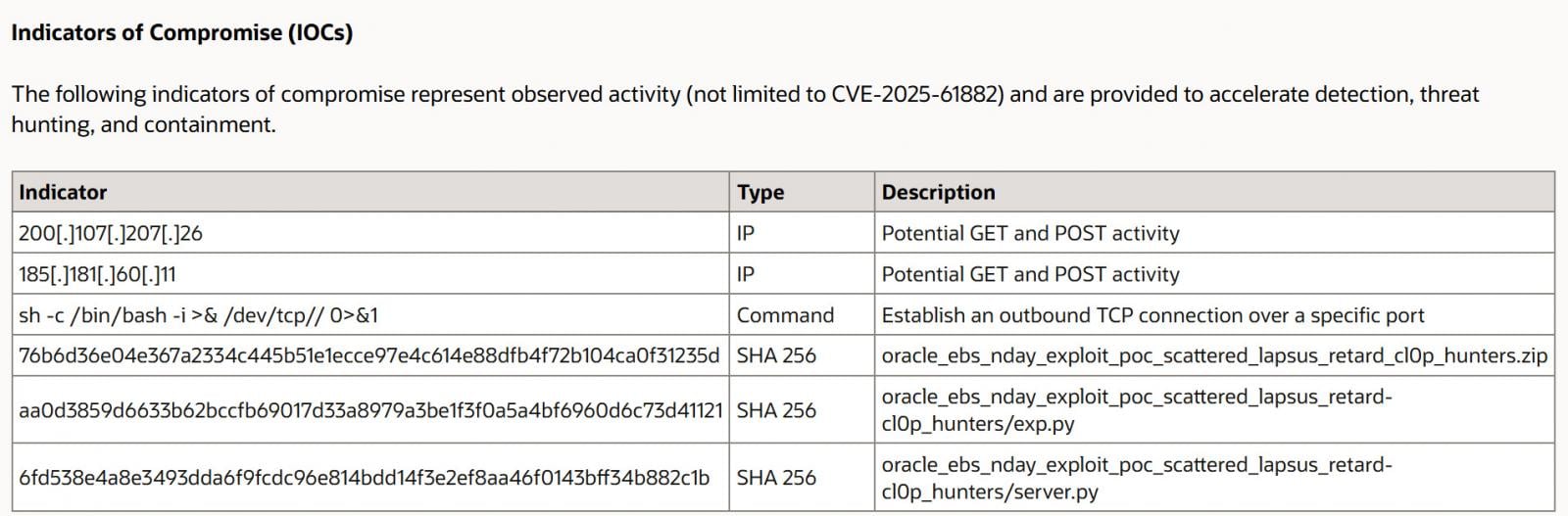
Source: Oracle
However, this is where things get confusing, primarily due to the silence of Oracle and other security vendors.
When the exploit was leaked, researchers at watchTowr Labs analyzed it, confirming it can be used to perform unauthenticated remote code execution on servers. This leaked exploit first targets the “/configurator/UiServlet” endpoint in Oracle E-Business Suite as part of the attack chain.
However, CrowdStrike and Mandiant later released reports that disclosed a completely different vulnerability that is believed to have been exploited by the Clop extortion gang in August 2025. This exploit first targets the “/OA_HTML/SyncServlet” endpoint.
Researchers at Mandiant also stated they saw exploitation activity similar to Scattered Lapsus$ Hunter’s leaked PoC exploit targeting UiServlet in July 2025.
Mandiant says that by updating to the latest patch released on October 4, customers are protected from all known exploit chains.
“Oracle released a patch on Oct. 4 for CVE-2025-61882, which referenced a leaked exploit chain targeting the UiServlet component, but Mandiant has observed multiple different exploit chains involving Oracle EBS and it is likely that a different chain was the basis for the Oct. 2 advisory that originally suggested a known vulnerability was being exploited,” explains Mandiant in its report.
“It’s currently unclear which specific vulnerabilities/exploit chains correspond to CVE-2025-61882, however, GTIG assesses that Oracle EBS servers updated through the patch released on Oct. 4 are likely no longer vulnerable to known exploitation chains.”
BleepingComputer and other cybersecurity researchers analyzed the patches released by Oracle for CVE-2025-61882. We found that they broke the Clop exploit by stubbing out the SYNCSERVLET class and by adding mod_security rules that prevent access to /OA_HTML/SyncServlet endpoint and various templates used to execute a malicious template.
However, there were no changes in the security update to fix the vulnerability exploited by ShinyHunter’s PoC, which was listed as an IOC for CVE-2025-61882. Therefore, it is unclear why Oracle even mentioned it in the advisory.
Furthermore, after CVE-2025-61882 was fixed, customers and researchers told BleepingComputer that tests indicate that at least the SSRF component of the leaked exploit still worked, even with current patches installed.
After installing this weekend’s update for CVE-2025-61884, these same researchers and customers tell BleepingComputer that the SSRF component is now fixed.
BleepingComputer has learned that the patch for CVE-2025-61884 now validates an attacker-supplied “return_url” using a regular expression, and if it fails, blocks the request. Because the regex allows only a strict set of characters and anchors the pattern, injected CRLF are rejected.
I suggest reading watchTowr Labs’s write-up to learn precisely how the leaked exploit works.
Still murky
At this point, it is unclear why Oracle patched the exploits like this and mismatched IOCs.
BleepingComputer contacted Oracle about its customers’ concerns, and either did not receive a response or was told they were declining to comment.
Mandiant told BleepingComputer that they are currently unable to answer our questions. CrowdStrike and watchTowr Labs referred us back to Oracle for questions related to the vulnerabilities.
If you are an Oracle E-Business Suite customer, it is strongly advised that you install all the latest updates, as the exploit chains and technical information are now publicly available.
If you are unable to install the latest update immediately, you should add a new mod_security rule that blocks access to /configurator/UiServlet to break the SSRF component of the leaked exploit until you can patch.
Source link







