
Threat actors claiming to represent the Medusa ransomware gang tempted a BBC correspondent to become an insider threat by offering a significant amount of money.
Cybersecurity correspondent Joe Tidy revealed in a story on the BBC that the hackers wanted to use his laptop to breach the British public-service broadcaster’s network and then ask for a ransom.
Once they got access to the BBC’s internal systems, the threat actor planned to steal valuable data and hold the organization to ransom. At least 15% of the paid ransom would go to Tidy for providing initial access.
Tidy says he was contacted in July over Signal by a cybercriminal named “Syndicate” (“Syn”), who initially offered him 15% of the paid ransom if he provided Medusa access to BBC systems.
Syn later tried to sweeten the offer with an additional 10%, saying that “their team could demand a ransom in the tens of millions if they successfully infiltrated the corporation.”
In continued attempts to lure Tidy to their side, Syn said “that their team could demand a ransom in the tens of millions if they successfully infiltrated the corporation,” which could mean that the journalist could never work again, living off the ransom cut.
Source: BBC
Medusa ransomware is an operation that emerged in January 2021 and gained a reputation with double-extortion attacks and the launch of an extortion portal in 2023.
In March, CISA published a report on Medusa, attributing to the gang more than 300 attacks on critical infrastructure organizations in the United States.
According to the agency, Medusa’s core operators recruit initial access brokers in cybercrime forums and darknet marketplaces, and they focus on the post-compromise phase.
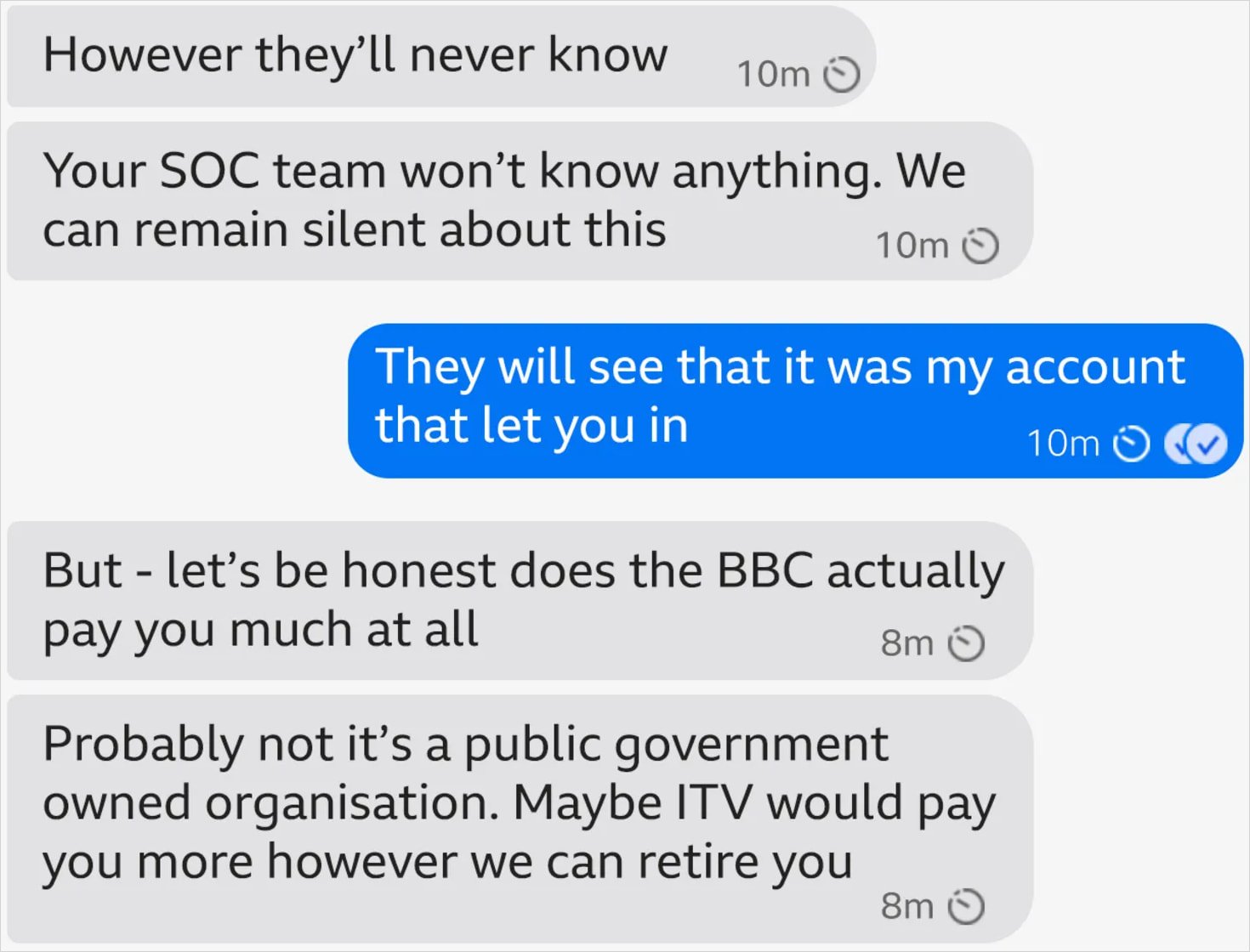
Tidy reports that the alleged ransomware group’s representative promised anonymity if he helped, citing several past cases that made headlines, which they claimed involved a rogue insider giving Medusa easy access to the target’s networks.
Underpaid, disgruntled, or simply unethical staff have caused millions in damages in exchange for a few hundred USD, and some threat actors count on that.
Ransomware gangs like LockBit have been exploring the potential of rogue employees willing to sell their access for several years now.
Syn even tried to persuade the journalist by offering 0.5 BTC (currently a little over $55,000) in escrow on a hacker forum before the hack even started.
“We aren’t bluffing or joking – we don’t have a purpose media wise we are only for money and money only and one of our main managers wanted me to reach out to you,” Syn told Tidy over Signal.
Tidy, who covers cybersecurity news, believes the threat actors likely mistook him for a cybersecurity employee at the BBC with high privilege access.
Syn pressed the journalist to execute a script, but when Tidy stalled, the journalist’s phone was flooded with two-factor authentication requests.
This is a tactic called MFA bombing, MFA fatigue, or MFA spam, where hackers automate log in attempts with the victim’s credentials to generate a barrage of authentication requests until the target gives up and allows the login.
Tidy didn’t give up, though. He contacted BBC’s information security team and, as a precaution, was disconnected completely from the organization’s infrastructure.
In a later message, the alleged Medusa representative apologized for the login requests and said that their offer was still available for a few days. However, when the journalist didn’t reply for a few days, the threat actor deleted their Signal account.
Source link







