
Cybersecurity company FuzzingLabs has accused the Y Combinator-backed startup, Gecko Security, of replicating its vulnerability disclosures and backdating blog posts.
According to the company, Gecko filed CVEs for two vulnerabilities that FuzzingLabs previously disclosed, and even “copied the PoCs, re-submitted them, and took the credit.”
Gecko Security has denied any wrongdoing, calling the allegations a misunderstanding over disclosure processes.
FuzzingLabs cries foul
A public dispute has erupted between two cybersecurity startups, FuzzingLabs and Gecko Security, after the former accused the Y Combinator-backed firm of copying its vulnerability discoveries and claiming credit for multiple CVE IDs.
“They copied our PoCs, claimed CVE IDs, and even back-dated their blog posts,” alleges FuzzingLabs on social media.
“This isn’t just about two CVEs, it’s about integrity in security research. We follow responsible disclosure. They waited for our public reports, copied the PoCs, re-submitted them, and took the credit.”
The vulnerabilities being referred to by FuzzingLabs are:
- Ollama (ollama/ollama) server authentication token stealing vulnerability: Original report filed Dec 24th 2024. Later assigned CVE-2025-51471.
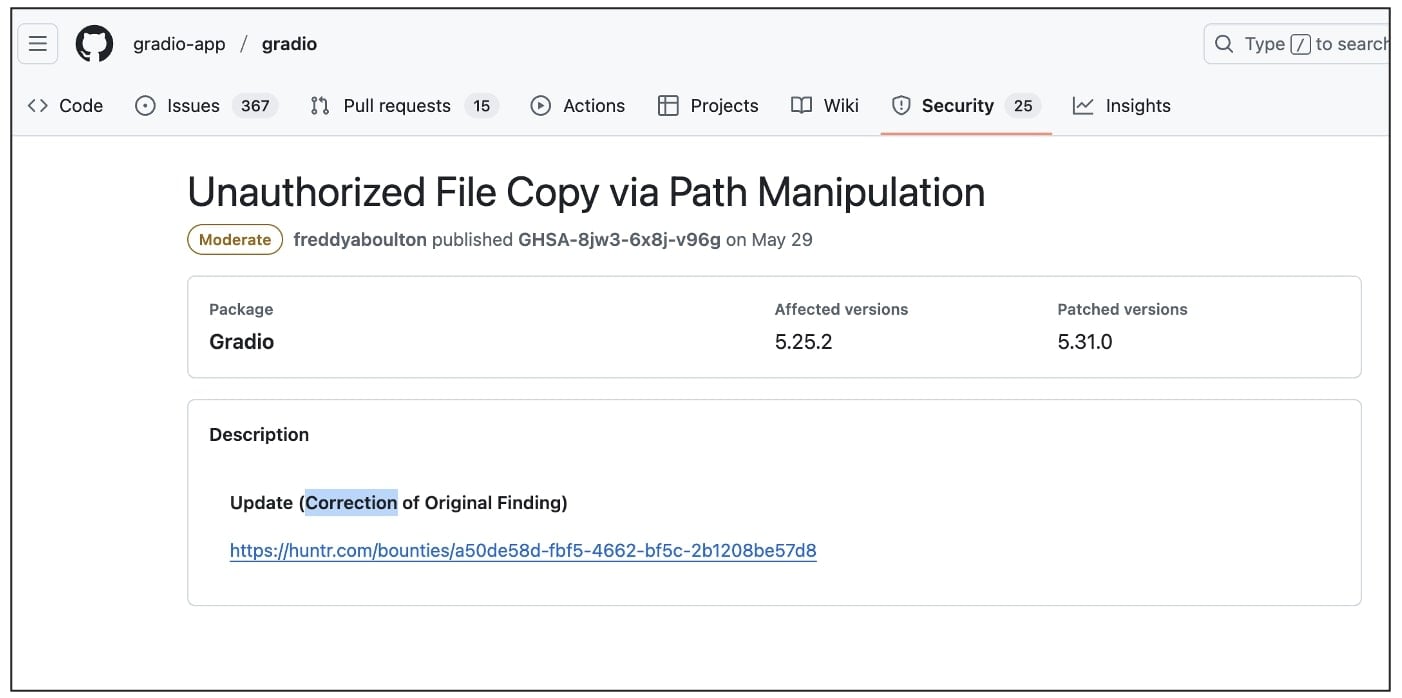
- Gradio (gradio-app/gradio) arbitrary file copy & Denial of Service (DoS) via flagging mechanism: Original report filed Jan 16th 2025. Later assigned CVE-2025-48889.
FuzzingLabs is a research-oriented cybersecurity company that has developed open-source tools that leverage AI for offensive security and fuzzing, the most prominent being FuzzForge. Gecko touts itself as the ‘AI Security Engineer for your Codebase’ that helps find and fix security vulnerabilities in your codebase.
In its investigation, FuzzingLabs found that pull requests (PRs) submitted by Gecko “were created after our legitimate Huntr reports went public” and that some vulnerabilities had multiple CVE IDs, one from their original hunter.dev report, and another from Gecko-submitted PRs.
FuzzingLabs further claims that Gecko backdated its blog posts to make them appear older than the real disclosures.
The company also says it has “indisputable evidence” of Gecko copying their exploits line-by-line because these contained “unique fingerprints we intentionally inserted to identify our work” in the event of plagiarism.
“And it’s not just us, at least 7 vulnerabilities on their website appear to be stolen from other researchers,” shared FuzzingLabs in the same thread, referring to their detailed findings with timestamps.
GitHub appears to have updated some advisories to credit FuzzingLabs’ original reports:
Gecko Security denies wrongdoing, credits researchers
Gecko has since edited its earlier blog post(s) crediting FuzzingLabs researchers Mohammed Benhelli and Patrick Ventuzelo, and updated publishing dates.
Gecko has characterized the situation as an unfortunate overlap, not intentional plagiarism, emphasizing that its workflow involves coordinating directly with project maintainers rather than through third-party platforms.
In a succinct response to social media posts calling out the startup responded:
“Disappointed to see public accusations without reaching out first, especially after launching a competitive product.
We work directly with maintainers via GitHub, not bounty platforms. Neither we nor the maintainers knew about your Huntr reports at the time, otherwise they would have been marked as duplicates.
We’ve publicly credited FuzzingLabs for the 2 CVEs where your findings came first, and we’re always happy to credit whoever finds them before we do.
The claim about stolen CVEs doesn’t hold up when many links you provided were already marked as ‘duplicate’ or ‘invalid’ on Huntr.”
Some members of the security community questioned Gecko’s explanation, while others pointed to the broader challenges of triaging duplicate vulnerability reports, especially as uncertainty looms over the future of CISA’s CVE program.
BleepingComputer reached out to both Fuzzing Labs and Gecko Security with additional questions on the matter. We did not hear back from Gecko.
In an email to us, FuzzingLabs’ Patrick Ventuzelo restated much of what the company had already outlined on social media, while welcoming Gecko’s updates following its posts.
“However, the original sequence of events … and back-dated blog entries raises [sic] broader concerns about their entire process,” Ventuzelo told BleepingComputer.
“They’ve referred to these cases as ‘duplicates,’ but having identical PoCs and unique markers we inserted ourselves directly collides with that narrative.”
The development highlights the nuances of credit and coordination in responsible vulnerability disclosure, especially when multiple researchers or companies may independently identify similar flaws across different platforms or ingest vulnerability data from the web.
Source link







