
For years, managed security service providers (MSSPs) followed a simple philosophy: that breaches were inevitable, and the best defense against them was rapid detection and response. This model, centered on Threat Detection, Investigation, and Response (TDIR), led to the rise of Managed Detection and Response (MDR) services that defined mainstream enterprise security for over a decade.
Today, MDR and its fundamental security strategy are simply no longer enough. Modern organizations operate across hybrid infrastructures and distributed ecosystems where new exposures appear almost continuously.
In these environments, waiting to be compromised is a luxury businesses can no longer afford. Executives and regulators alike now view cybersecurity as a business risk. They expect proof that defenses can prevent incidents, not just respond to them.
This expectation has driven a focus back from reaction to preemption, and at the center of that shift stands a new generation of platforms built to unify and operationalize exposure management.
Why Organizations Are Shifting Left of Traditional Managed Services
Traditional MDR offerings focus on detecting and mitigating attacks already in motion. While essential, they address symptoms rather than root causes. The modern enterprise demands the opposite: continuous identification and validation of weaknesses before adversaries can exploit them.
This “shift left” approach is being driven by several intersecting forces.
First, regulatory and executive scrutiny has intensified over the last several years. CISOs must demonstrate measurable risk reduction tied to business outcomes, not just tool deployment.
Second, cloud migration, third-party integrations, and AI automation have expanded attack surfaces far beyond human-scale visibility.
And third, sophisticated adversaries now strike in the narrow window between vulnerability disclosure and patching, weaponizing new flaws faster than defenders can respond.
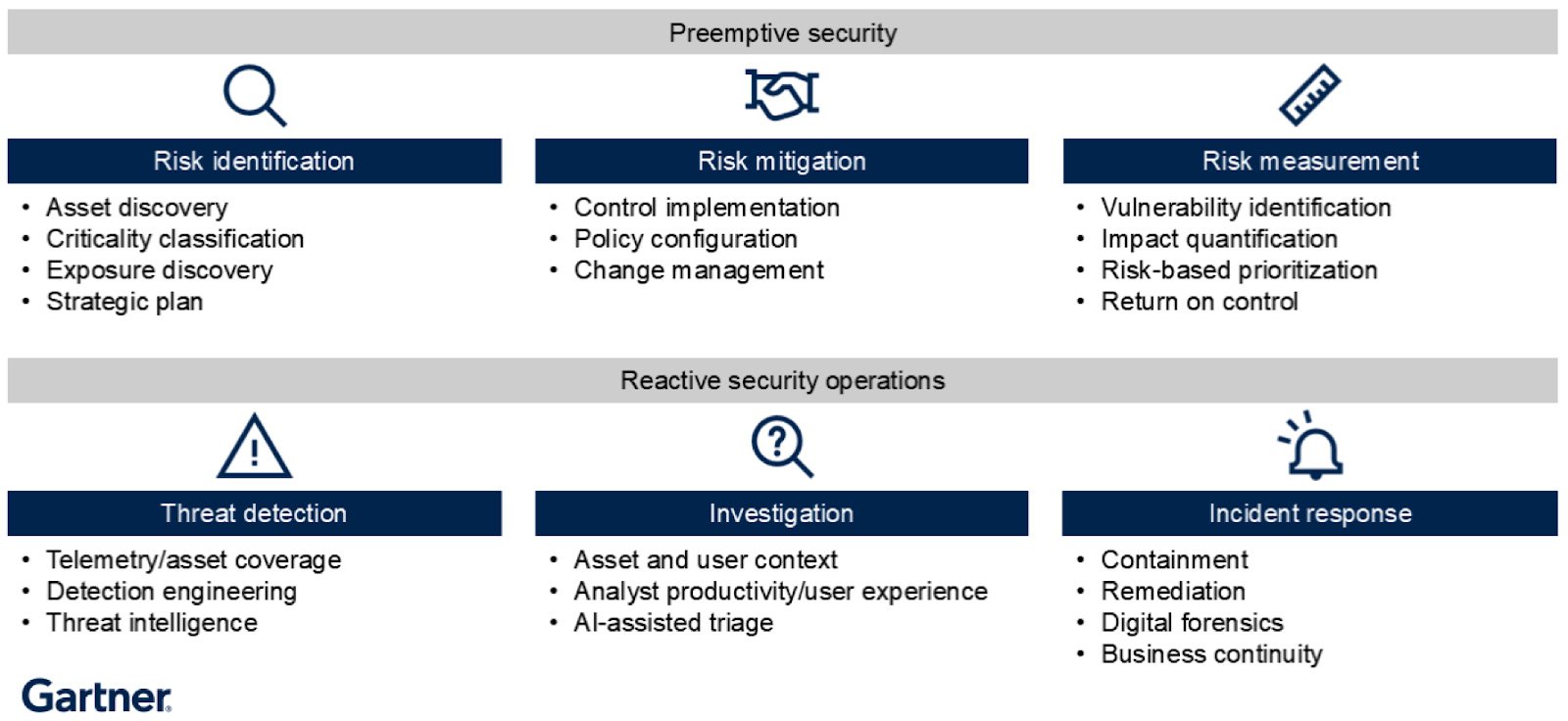
This image is taken from Gartner’s Emerging Tech: Pivot to Preemptive Exposure Management Services to Grow Revenue report. Gartner, Emerging Tech: Pivot to Preemptive Exposure Management Services to Grow Revenue, Peer Contributors, 24 July 2025.
This has increasingly led to a call for unified, evidence-based visibility into where organizations are truly at risk and a better understanding of how those risks translate into business impact. Enter Unified Exposure Management Platforms.
See how the Picus Security Validation Platform operationalizes Unified Exposure Management by continuously testing your controls, proving exploitability, and guiding remediation.
Discover where your defenses stand and strengthen what matters most.
Unified Exposure Management Platforms Explained
Unified Exposure Management Platforms (UEMPs) continuously discover assets and weaknesses, determine which ones are exploitable in an organization’s environment, and coordinate remediation across teams. They bring together what were once separate practices, such as asset discovery, vulnerability assessment, validation, and remediation, into one continuous process that connects technical evidence directly with business outcomes.
Traditional tools each solve part of the problem. Vulnerability scanners identify weaknesses but cannot prove exploitability. Penetration tests provide realistic assessments, but only in snapshots. Risk quantification models financial exposure but lacks a technical context. UEMPs merge these perspectives, closing the gap between theoretical risk and real resilience.
At their core, UEMPs perform three things continuously: they identify exposures, validate exploitability, and mobilize fixes. This creates a feedback loop that aligns security operations with enterprise risk management. Instead of more and more (and more!) data, security teams get more relevant, higher-quality, actionable data that’s contextualized, prioritized, and verified.
For example, imagine a development team leaves an unused S3 bucket publicly accessible, exposing configuration files that contain hard-coded credentials. An attacker could use those credentials to access internal systems and exfiltrate sensitive data.
A Unified Exposure Management Platform detects the exposed bucket, validates exploitability by simulating credential extraction and data exfiltration through Breach and Attack Simulation (BAS), and confirms that an attacker could reach privileged assets.
It then provides step-by-step remediation guidance to address the underlying misconfigurations. In the next validation cycle, this type of simulated attack fails to progress, offering clear, verifiable proof that the exposure path has been closed.
How Unified Exposure Management Platforms Work
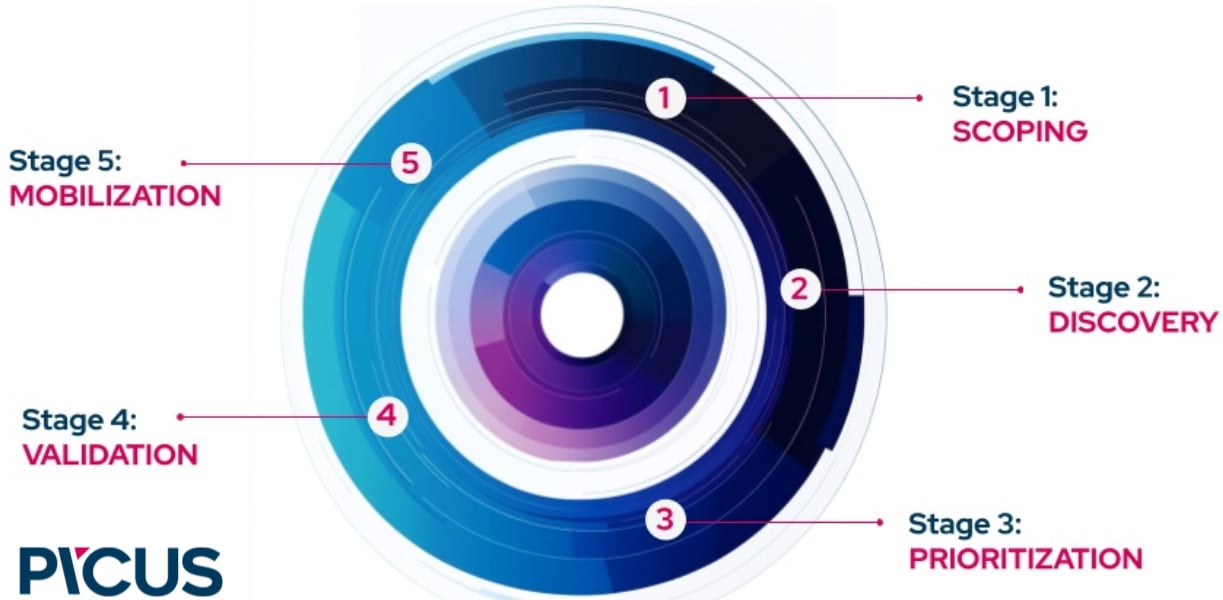
Unified Exposure Management Platforms put the Continuous Threat Exposure Management (CTEM) model into action by turning its five stages into an ongoing, repeatable process.
-
Scoping identifies the assets, dependencies, and risks that matter most, ensuring that exposure management supports operational priorities instead of technical checklists.
-
Discovery continuously maps assets, configurations, and vulnerabilities across servers, endpoints, identities, APIs, code repositories, and external integrations, bringing every potential entry point into a single repository.
-
Prioritization determines which exposures pose the greatest risk. It correlates severity, exploit likelihood, control coverage, and asset value to produce a ranked backlog. This step forms hypotheses about probable attack paths but does not yet measure control effectiveness.
-
Validation converts those hypotheses into evidence. UEMPs orchestrate Breach and Attack Simulation to test defensive layers and run Automated Penetration Testing to chain conditions end-to-end, proving which attack paths are truly exploitable. This process calibrates risk scores with organizational fact, revealing where prevention and detection controls fail in practice.
-
Mobilization transforms these findings into tangible actions. The platform coordinates remediation by automating patching, refining detection rules, and supporting teams as they implement fixes. This phase brings preemptive security to life, reducing potential dwell time from identification to mitigation.
Through these stages, UEMPs present a unified, dynamic view of an organization’s security posture. They connect vulnerabilities, misconfigurations, and control gaps into one risk fabric and translate results into tangible business terms such as risk reduction, resilience, and return on investment.
The Future: Security That Anticipates
The shift toward preemptive exposure management redefines what effective security means. The ultimate measure of readiness is no longer how quickly an organization responds, but how well it prevents.
Unified Exposure Management Platforms embrace this philosophy. By uniting discovery, validation, and remediation in a single operational workflow, they transform security from a reactive scramble into a proactive capability that anticipates, adapts, and proves its effectiveness.
Picus Security, recognized by Gartner as a sample vendor in this emerging category, delivers a platform designed to operationalize every stage of Unified Exposure Management.
Explore the Picus Security Validation platform now and request a demo to see how we help correlate siloed data sources by gathering and managing asset intelligence, vulnerabilities, and threats in one platform.
Sponsored and written by Picus Security.
Source link






